CustomActiveScanForZAP
A ZAP AddOn ActiveScan for detecting SQL injections. Real Web application page has dynamic contents such as special sale products list or CSRF token, which is not affected by input parameters. The web application vulnerability scanner manipulates input parameters to detect vulnerabilities by affecting page content. The scanner may fail to detect vulnerabilities if the dynamic content of the web page has contents which is unaffected by the input parameters. Therefore, this CustomActiveScan uses LCS (Longest Common Sequece) algorithm to remove these unnecessarily dynamic content. Due to this method, this scanner has a superior vulnerability detection capability.
how to remove these dynamic contents which is not affected input parameters.
LCS(Longest Common Sequence) algorighm extracts the content that is common to two array elements. For example, you have a web page that contains a CSRF token. The CSRF token has a unique value for each http request. To erase this token, this addon sends two identical http requests and computes the response LCS of the two requests. LCS remove the different token values from the two responses as follows:
[response1]
<form action="add.php" method="POST">
<input type="hidden" name="token" value="dbc8ee88f64bf794505ef74e41d6e5a4">
<input type="submit" value="Complete">
</form>
[response2]
<form action="add.php" method="POST">
<input type="hidden" name="token" value="bcb138585064356efa927ab196cbf8ec">
<input type="submit" value="Complete">
</form>
[LCS]
<form action="add.php" method="POST">
<input type="hidden" name="token" value=">
<input type="submit" value="Complete">
</form>
- Before calculating the LCS, this addon splits the response content by whitespace/JSON/HTML delimiters or characters and stores it in an array.
SQL injection test some results.
| SQL injection Detection rate (Detected/Total) | CustomActiveScan ForZAP 0.8.3 | Active Scanner Rules(alpha) 44.0.0 | Active Scanner Rules 57.0.0 | Advanced SQLInjection Scanner 15.0.0 |
|---|---|---|---|---|
| 100% (14/14) | 50% (2/4) | 20% (2/10) | 40% (4/10) |
Prerequisite
- ZAPROXY ver 2.13.0 or later
- java ver 11 or later
Download & Building
The add-on is built with [Gradle]: https://gradle.org/
To download & build this addon, simply run:
$ git clone https://github.com/gdgd009xcd/CustomActiveScanForZAP.git
$ cd CustomActiveScanForZAP
$ ./gradlew addOns:customactivescan:jarZapAddOn
The add-on will be placed in the directory CustomActiveScanForZAP/addOns/customactivescan/build/zapAddOn/bin
$ cd addOns/customactivescan/build/zapAddOn/bin
$ ls
customactivescan-alpha-0.0.2.zap
$
- Gradle builds may fail due to network connection timeouts for downloading dependencies. If you have such problems, please retry the gradlew command each time. or you can download addon file from release page
Install
1)Start ZAPROXY in your PC’s Desktop.
2)Install add-on customactivescan-alpha-N.N.N.zap file according to the ZAP add-on installation method (example: File menu “Load add-on file”).
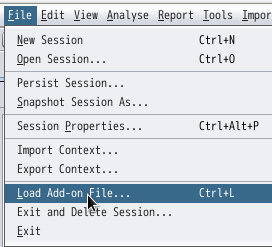
3)restart zap(sorry, currently this addon does not work unless restart zap after install it.)
how to use
This is automatically called when you start active scannig after already installed default scanners. If you have any doubts whether this scanner is actually being called, you can import the CustomScan.policy file. This policy forces the use of CustomScan when invoking active scan. using guide is follows:
1) download CustomScan.policy
2) select menu [Analyse->Scan Policy Manager->import], and load CustomScan.policy file.
3) when you start scan, select policy [Custom Scan].
Information on how to use can be found at the following link:
Basic Usage
